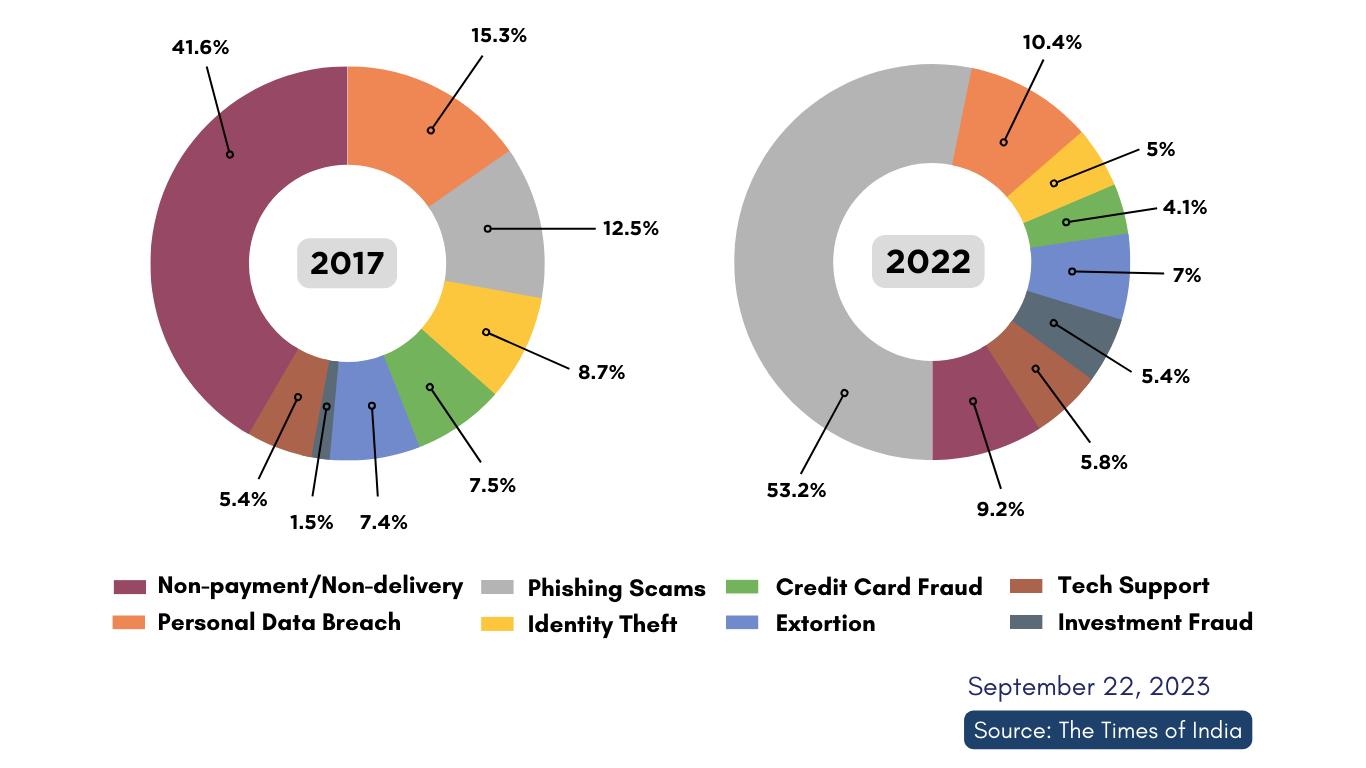
SHARE OF CYBER ATTACK BY TYPE
What is Phishing
Secure your Data, applications and workloads to the cloud. When it comes to adopting cloud technology, security is the most critical issue. Many organizations are in fear that their data is not secure on cloud. Cloud security protects your business where it lives. Your applications are in the cloud and clients are all over the place. Your security can't be attached to the data center.

Simulation Based Employee Awareness Program
Simulation- based platform to helps identify employees who are targeted by cyber criminals and train them to counter the phishing attacks, hence, strengthening the weakest link in the organization.
The Employee Awareness Program encourages awareness about various information security topics followed by training and evaluation.
Phishing Is A Serious Threat To your Business
The Employee Awareness Program encourages awareness about various information security topics followed by training and evaluation.
85%
of organization have experienced a phishing attack!
REDUCE RISK
81%
of the phishing attacks involved email domain spoofing
TEST EMPLOYEES
30%
of phishing messages were opened by the employees
CONDUCT TRAINING
Benefits of simulation-based anti-phishing program
A simulation-based anti-phishing program offers several benefits for organizations aiming to enhance their cybersecurity posture:
Realistic Training Environment
It provides a controlled environment where employees can experience phishing attempts without compromising on real environment. This hands-on experience helps them recognize phishing tactics more effectively.
Behavioral Change
A good simulating portal can track and analyze employee responses. This data helps identify weak links within the organization and allows focused training to improve behavior and response rates.
Risk Assessment
It enables organizations to assess their vulnerabilities to phishing attacks based on employee reaction to simulated threats. This assessment helps in understanding areas for improvement and allocating resources accordingly.
Education & Awareness
The portal provides immediate results followed by guidance to employees who fall for simulated phishing attempts. This helps in raising awareness about phishing tactics and best practices for identifying them.
Customization and Adaptability
Organizations can customize the simulations based on their specific requirements. This ensures that training remains relevant and effective.
Continuous Improvement
Through regular simulations and analysis, the portal supports continuous improvement of cybersecurity readiness. It allows organizations to evolve their training programs based on emerging phishing trends and employee feedback.
Compliance and Reporting
The organized reporting features help organizations demonstrate compliance with cybersecurity standards and regulations with detailed analytics and metrics that can be used for audits and reporting purposes.
Cost-Effectiveness
Investing in a simulation-based portal can be cost-effective compared to dealing with the outcome of a successful phishing attack. It helps mitigate the risk of data breaches and other cyber incidents that could incur significant financial and reputational costs.
Planning a Simulation based training
Overall, a simulation-based anti-phishing portal empowers the organizations to train their employees effectively, reduce vulnerabilities, and strengthen their overall security posture against phishing attacks.
Implementing a simulation-based anti-phishing training program involves steps to ensure its effectiveness and integration into the organization's cybersecurity framework. Here’s a structured approach:
Program Assessment and Planning:
- Identify Objectives: Define the specific goals of the training program, such as reducing click rates on phishing emails, improving incident reporting, or raising overall awareness.
- Assess Current State: Evaluate existing cybersecurity awareness levels and any past incidents related to phishing. This baseline assessment helps tailor the training program to address specific weaknesses.
Selecting the right Simulation Platform:
- Research and Choose a Platform: Select a simulation-based anti-phishing training platform that suits your organization’s needs based on factors such as simulation realism, customization options, reporting capabilities, and user interface.
Customization of the Program:
- Develop Scenarios: Create a variety of realistic phishing scenarios by using the threat vector (e.g., email, phone, social engineering) that reflects the potential threats faced by your organization.
- Customize Training: Tailor the simulations to the roles and responsibilities of different employee groups within your organization.
Implementation and Delivery:
- Launch the Program: Communicate the launch of the anti-phishing training program to all employees, emphasizing its importance and goals.
- Schedule Simulations: Plan a schedule for rolling out the simulations, ensuring that they are spread out over time to maintain engagement and effectiveness.
- Provide Access and Support: Ensure that employees and administrators have access to the simulation platform along with any technical support.
Simulation Program Execution:
- Execute Simulations: Run the planned phishing simulations according to the schedule. Monitor employee responses and collect data on click rates, opening rates, credential submissions and other metrics.
- Provide Feedback: Offer feedback to employees who interact with the simulations, provide training when they fall for the phishing attempt or report it correctly.
Analysis and Improvement:
- Evaluate Results: Run the planned phishing simulations according to the schedule. Monitor employee responses and collect data on click rates, opening rates, credential submissions and other metrics.
- Identify Gaps: Identify any weaknesses areas and potential risks.
- Improvement Steps: Based on the analysis, refine the training program by updating scenarios, adjusting training materials, or providing additional targeted training for specific groups.
Continuous Monitoring:
- Monitor Trends: Stay updated on emerging phishing techniques and cybersecurity threats. Update training content regularly to keep the program relevant.
- Refresher Sessions: Schedule regular refresher sessions to reinforce learning and ensure that awareness remains high among employees.
Reporting and Compliance:
- Generate Reports: Generate comprehensive reports on training effectiveness, employee performance, and overall cybersecurity posture. Maintain Compliance documentation of training activities and results to align with the cybersecurity regulations and standards.
By following these steps, organizations can establish a robust simulation-based anti-phishing training program that effectively educates employees, reduces susceptibility to phishing attacks, and strengthens overall cybersecurity defenses.
Learn How Anti-Phishing Simulation Helps Protect Your Organization