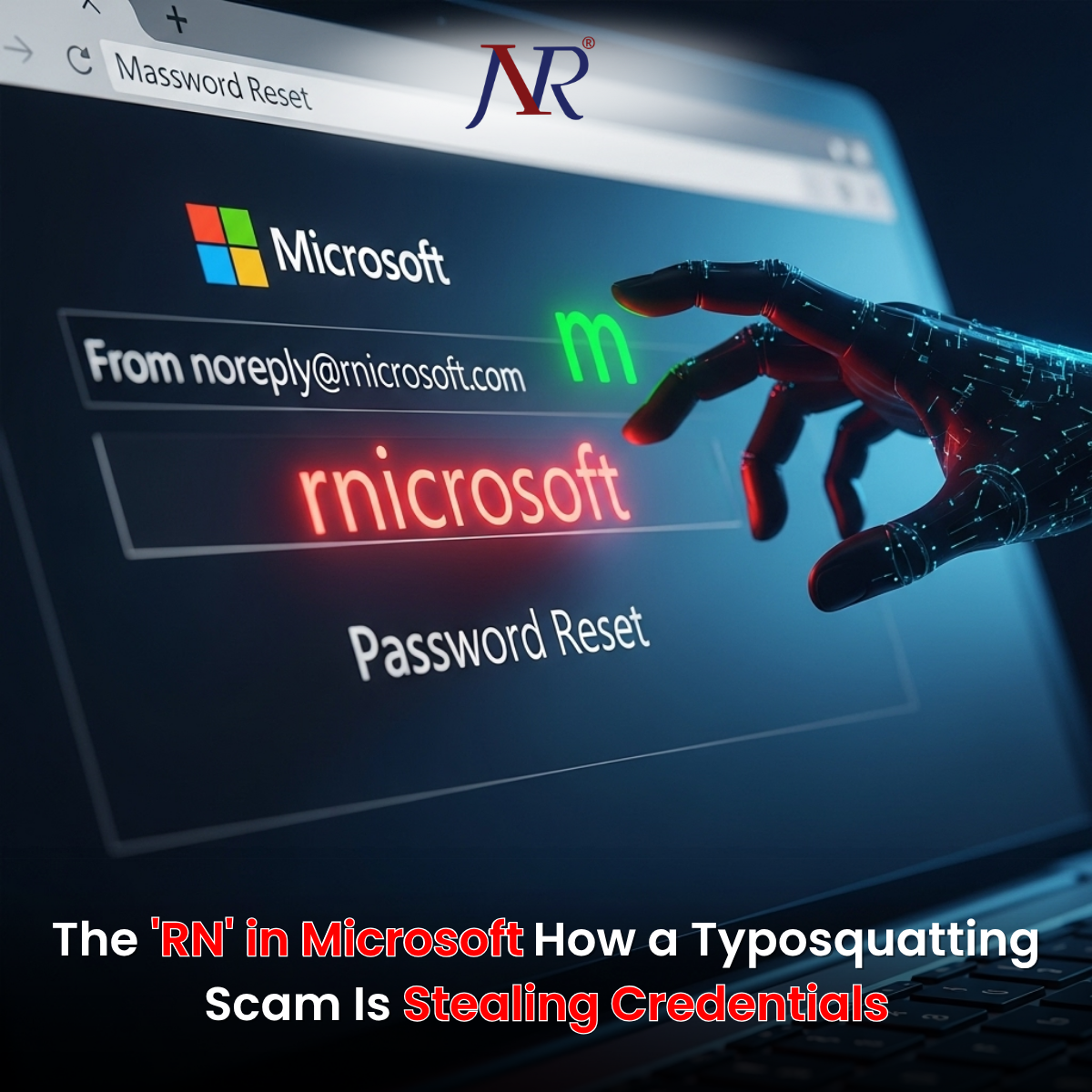

A deceptively simple yet highly effective phishing campaign is exploiting human visual perception to steal credentials from unsuspecting users. The scam, which leverages a decade-old fake domain "rnicrosoft.com," replaces the letter "m" in Microsoft with the characters "r" and "n" placed side-by-side—creating a near-perfect visual illusion that has fooled countless victims and sparked viral discussions across social media platforms.
When X (formerly Twitter) user Jeremy shared a screenshot of a suspicious password reset email, he highlighted a detail that sent chills through cybersecurity communities worldwide. The sender address displayed "noreply@rnicrosoft.com"—a domain that appears completely legitimate at first glance. Only upon close inspection does the deception become apparent: the lowercase letters "r" and "n" combined perfectly mimic the appearance of the letter "m."
"The scammers are evolving," Jeremy wrote in his viral post, which quickly garnered thousands of responses from users who admitted they would have fallen for the trap. One commenter confessed, "It took me a few seconds to spot it. Crazy." Another added, "If I got that mail, my account would've been compromised instantly."
The email itself was meticulously crafted to mirror authentic Microsoft communications, featuring accurate branding, official-looking layout, professional language, and urgent messaging about unauthorized password reset attempts. Every element was designed to trigger immediate action before victims could scrutinize the sender's details.
Public domain records reveal that rnicrosoft.com has existed since 2012, originally registered under Park HyungJin based in South Korea. The domain is currently set to expire in March 2026, though cybersecurity researchers note it has been periodically renewed and repurposed for various phishing campaigns throughout its existence.
Users across Reddit and LinkedIn report encountering this same domain in previous years, always with similar password reset themed messages designed to harvest Microsoft account credentials. The campaign's persistence demonstrates a troubling reality: successful phishing tactics rarely disappear—they simply lie dormant before resurfacing with new victims.
This type of deception falls under two related categories of cyberattack: homograph attacks and typosquatting. Homograph attacks exploit visual similarities between different characters to create lookalike domains, while typosquatting involves registering domain names that closely resemble legitimate sites to catch users who make typing errors or don't look carefully.
The "rn" to "m" substitution represents one of the most effective homograph techniques because of how closely these character combinations resemble each other in many standard fonts. Other common homograph substitutions include replacing lowercase "l" with uppercase "I," using zero (0) instead of the letter O, or swapping numbers that look like letters.
According to the Cybersecurity and Infrastructure Security Agency (CISA), approximately 70% of malicious attachments or links in phishing emails successfully bypass network protection systems. This alarming statistic highlights why human vigilance remains the critical last line of defense against sophisticated social engineering attacks.
Cybercriminals understand that most people process email addresses through rapid visual pattern recognition rather than careful character-by-character analysis. When an email appears to come from a trusted source like Microsoft, recipients typically focus on the message content and calls-to-action rather than scrutinizing the sender domain.
The scam's effectiveness is amplified by several psychological factors:
The recent viral spread of Jeremy's screenshot triggered extensive discussions across online communities. Reddit users analyzing the email expressed both admiration for the scam's cleverness and alarm at its effectiveness. One highly-upvoted comment read, "Damn bro, the scammer is really using 200% of his brain."
Multiple users admitted they only noticed the deception after reading explanatory comments, demonstrating how easily the trick bypasses normal scrutiny. One commenter noted, "I only realised it after reading the description," while another added, "What do we do? Our generation is more into kick streams than finding real solutions."
Cybersecurity experts recommend several defensive measures to protect against homograph and typosquatting attacks:
The rnicrosoft.com campaign exemplifies how cybercriminals continuously refine social engineering tactics to exploit human psychology and technological trust systems. As artificial intelligence and machine learning tools become more accessible, experts anticipate even more sophisticated phishing campaigns that perfectly replicate authentic communications.
The incident underscores a critical cybersecurity principle: technical defenses alone cannot prevent all attacks when human decision-making remains the final gateway. Organizations and individuals must cultivate a culture of healthy skepticism, where verification becomes second nature rather than an afterthought.
As one security researcher noted in response to the viral post, "This is becoming scary." Indeed, as scammers continue evolving their techniques with near-invisible deceptions like the "rn" to "m" substitution, the line between legitimate and fraudulent communications grows increasingly blurred—making vigilance, education, and careful verification more essential than ever.